Analysis Date: January 7, 2026
Methodology: Static analysis only
Sample: f6f7a37b49310287a253dbdf81e22f0593f44111215ca9308e46d2c68516196f
TL;DR
In-depth analysis of GLOBAL GROUP ransomware (RaaS), revealing:
- An encrypted
.configsection using a custom XOR + LCG algorithm - Hybrid encryption: Curve25519 (ECDH) + SHA-512 (KDF) + HC-128 (stream cipher)
- The “hash” at config offset 0x843 is actually the builder’s Curve25519 public key
- Three encryption modes based on file size (including a “panic” mode)
- Per-file ephemeral keys with proper asymmetric cryptography
- A builder structure allowing per-victim custom configs
Intro - Personal thoughts
I tend to approach malware analysis from a low‑level, technical perspective. Rather than focusing on APT naming, MITRE mappings, or high‑level threat classifications, I’m mostly interested in how malware actually works internally. I enjoy taking things apart: understanding custom algorithms, configuration formats, encryption routines, and the overall logic implemented in the binary.
I also tend to avoid classic dynamic analysis whenever possible. Between anti‑VM tricks, sandbox detection, and the inherent risk of executing real malware, I find static analysis and low‑level emulation (using tools like Unicorn or Qiling) to be a safer and more reliable way to study samples. This kind of approach fits me better: it allows me to focus on reversing the code itself, step by step, without relying on runtime behavior or external classifications.
¯\(ツ)/¯
Why
I decided to face a ransomware from a reversing point of view. While scrolling on X I saw a post from @RakeshKrish12 saying :
1 | 🚨#Global #Ransomware is back as AWARE! |
And just choose this one randomly :D
Reconnaissance: That Section Shouldn’t Be There
Opening the binary in a hex editor, something immediately catches the eye:
1 | $ xxd f6f7a37b49310287a253dbdf81e22f0593f44111215ca9308e46d2c68516196f | grep -A5 ".config" |
A .config section? In a C/C++ compiled executable? That smells like a custom build system or… a ransomware-as-a-service (RaaS) embedding per-victim configs.
Quick check with PE-bear:
- Section name:
.config - Virtual Address:
0x43e000 - Raw Size:
0x864(2148 bytes) - Characteristics:
0x40000040(READ | INITIALIZED_DATA)
Let’s see what’s inside this section:
1 | $ dd if=f6f7a37b49310287a253dbdf81e22f0593f44111215ca9308e46d2c68516196f bs=1 skip=$((0x39a00)) count=64 | xxd |
WTF?! This looks like random noise. Entropy check:
1 | import math |
7.98 bits/byte = near-perfect random = it’s encrypted.
Config Decryption: Custom XOR + LCG
Locating the Decryption Code
Searching for references to the .config section in Binary Ninja, we land on a large function at 00402940 doing suspicious things:
1 | // At 0x402d6c - Searching for .config section |
OK so the malware dynamically searches for its own .config section. Smart - no hardcoded offsets.
The Decryption Algorithm
Here’s the decryption code :
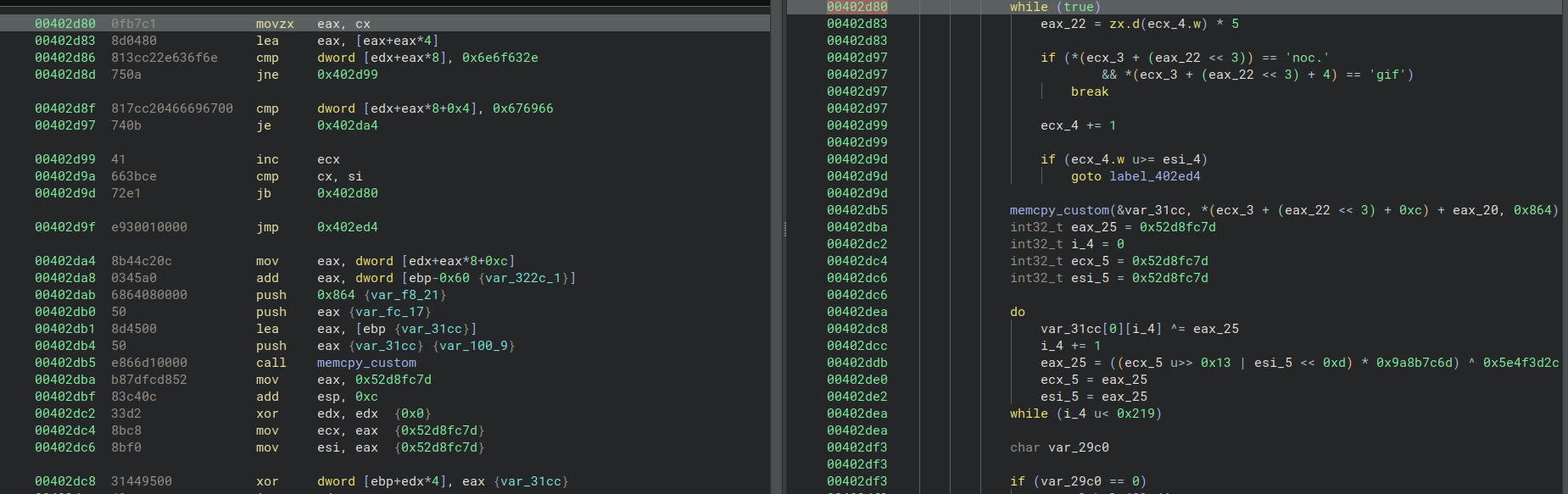
It’s a custom Linear Congruential Generator (LCG)! The formula:
1 | key[n+1] = (ROR(key[n], 13) × 0x9a8b7c6d) ⊕ 0x5e4f3d2c |
With:
- Initial seed:
0x52d8fc7d - Multiplier:
0x9a8b7c6d - XOR constant:
0x5e4f3d2c
Python Decryptor Implementation
1 | #!/usr/bin/env python3 |
Output:
1 | b'\n\x00\x00\x00Your network has been breached. Data has been encrypted and stolen...' |
BOOM! We got the decrypted config. The first DWORD (0x0000000A = 10) is the encryption percentage - we’ll see why it’s crucial in the encryption modes section.
Decrypted Config Structure
By analyzing the code that parses the config, we can try to reconstruct and guess the complete structure:
1 | struct GlobalGroupConfig { |
Critical discovery: The 32 bytes at offset 0x843 aren’t a “hash” at all - it’s the builder’s Curve25519 public key. This is the foundation of the ransomware’s asymmetric encryption scheme.
Example of decrypted config (excerpt):
1 | Offset Content |
Hybrid Encryption Architecture
GLOBAL GROUP uses hybrid encryption - combining asymmetric (Curve25519) and symmetric (HC-128) cryptography. This is the same approach used by modern secure protocols like TLS.
Why Hybrid?
Pure symmetric encryption (bad):
- Ransomware has a hardcoded secret key → reverse engineer once, decrypt everything
- Same key for all victims → one break compromises all
Hybrid encryption (good):
- Ransomware only has the builder’s public key (can’t decrypt with this)
- Each file gets a unique ephemeral key pair
- Only the builder (with the private key) can decrypt
- Reverse engineering the binary is useless without the private key
Complete Encryption Flow (Per File)
Let’s trace the entire encryption process for a single file:
Step 1: Generate Ephemeral Key Pair (0x401f11)
1 | // Generate random private key (unique for THIS file) |
This clamping is the signature of Curve25519:
- Bits 0-2 cleared: avoids small subgroup attacks
- Bit 254 set, bit 255 cleared: forces key into correct range
Result: 32 random bytes that form a valid Curve25519 private key.
Step 2: ECDH Key Exchange
1 | // First ECDH: Generate ephemeral public key |
sub_40fdc0 is the X25519 scalar multiplication function.
Critical point: This shared secret can be computed two ways:
- Ransomware (encryption):
X25519(ephemeral_private, builder_public) - Builder (decryption):
X25519(builder_private, ephemeral_public)
Both produce the same 32-byte shared secret. This is the magic of ECDH!
Step 3: Key Derivation with SHA-512 (0x401f75)
1 | // Derive 64-byte key from 32-byte shared secret |
sub_40b830 is a SHA-512 based KDF with custom 64-byte constants. Analysis of the underlying functions reveals:
sub_40b390= SHA512_Update (hashes input data)sub_409ed0= SHA512_Transform (compression function with characteristic rotations)sub_40b500= SHA512_Final (padding + output)
The KDF adds an extra security layer and expands the key material to 64 bytes.
Step 4: HC-128 Initialization (0x401f94)
1 | // Initialize HC-128 stream cipher |
HC-128 is an eSTREAM finalist - a battle-tested stream cipher. Identified by:
- Two tables (P & Q) of 512 elements each
- Characteristic rotations: ROR(23,10,8) for P-table, ROR(22,9,24) for Q-table
- 64-byte keystream blocks generated per call
This is kinf of serious cryptography.
Step 5: File Encryption
1 | // For each 64-byte block |
Classic stream cipher operation: XOR plaintext with pseudo-random keystream.
Step 6: Write Footer (0x40261a)
1 | // Append 0x258 bytes (600 bytes) to encrypted file |
Why the footer is essential: Without the ephemeral public key, even the builder can’t decrypt - there’s no way to recalculate the shared secret!
Decryption Process (Builder Side)
1 | ┌─────────────────────────────────────────────────────────┐ |
Why This must be “Unbreakable” Without the Private Key
❌ Can’t extract the builder’s private key - it’s never in the binary
❌ Can’t brute force Curve25519 - 2²⁵⁶ possible keys
❌ Can’t reuse keys across files - each file has unique ephemeral keys
❌ Can’t attack the crypto - Curve25519, SHA-512, and HC-128 are all cryptographically sound
✅ Only the builder with the private key can perform the ECDH and recover the shared secret
Encryption Modes: From Panic to Methodical
The ransomware adapts its strategy based on file size. By analyzing the code at 0x402019 and following, we identify three distinct modes.
Mode 1: Files < 5 MB - Full Encryption
1 | if (fileSize < 0x500000) { // 5 MB |
Strategy: Full encryption. Small files are completely destroyed.
Mode 2: Files 5-70 MB - Spaced Encryption
1 | else if (fileSize >= 0x500000 && fileSize <= 0x4600000) { // 5-70 MB |
Strategy: Sampling encryption. Saves time while making the file unusable (imagine a video or database with encrypted holes every 10 MB).
Mode 3: Files > 70 MB - PANIC Mode
This is where it gets interesting. For large files, the malware looks at the encryption_percentage from the config (remember: 0x0A = 10%).
1 | else { // > 70 MB |
Strategy: On a 10 GB file with encryption_percentage = 10, the ransomware will encrypt only 1 GB spread uniformly. This drastically speeds up the attack (seconds instead of minutes) while making files unrecoverable.
Why “PANIC”? Because this mode is probably designed for scenarios where the attacker knows they have little time (imminent detection, admin arriving, EDR about to trigger). They sacrifice completeness for speed.
Mode Comparison
| File Size | Mode | Strategy | Time (estimate) |
|---|---|---|---|
| < 5 MB | Full | 100% encrypted | ~1-2 seconds |
| 5-70 MB | Spaced | 4 KB blocks / 10 MB | ~0.5-1 second |
| > 70 MB | Panic | 10% uniformly | ~0.1-0.5 seconds |
On a large server with TBs of data, panic mode allows corrupting everything in minutes instead of hours.
The Footer: Decryption Ticket (Maybe)
At the end of each encrypted file, the ransomware writes a footer of 0x258 bytes (600 bytes):
1 | // At 0x40261a - Footer writing |
This footer contains:
- The ephemeral public key generated for this file (32 bytes)
- Encryption metadata (mode used, offsets, etc.)
- Probably a hash/checksum
Why is this important? To decrypt, the attacker (who possesses the private key corresponding to the public key in the config) can:
- Read the encrypted file’s footer
- Extract the ephemeral public key
- Perform ECDH with their private key to recalculate the shared secret
- Regenerate the same HC-128 key
- Decrypt the file
This is proper asymmetric crypto No secret key stored locally - impossible to decrypt without the builder’s private key.
(Assuming correct implementation and no side-channel / implementation flaws that I did not verify :D)
IOCs and Detection
Analyzed File
1 | SHA256: f6f7a37b49310287a253dbdf81e22f0593f44111215ca9308e46d2c68516196f |
Behavioral Indicators
Search for .config section:
1 | if (!strcmp(section->Name, ".config")) |
Characteristic crypto calls:
CryptGenRandomfor key generation- Curve25519 scalar multiplication (clamping pattern)
- Encryption loops with HC-128 patterns
File modifications:
- Custom extension added
- 0x258 byte footer
- File attribute modifications (
SetFileAttributesW)
Cryptographic stuff
✅ Modern hybrid encryption: Curve25519 ECDH + SHA-512 KDF + HC-128 stream cipher
✅ Proper key management: Per-file ephemeral keys, no secrets in binary
✅ Battle-tested algorithms: eSTREAM finalist (HC-128), RFC 7748 (Curve25519)
✅ No crypto mistakes: Correct clamping, proper IV/key separation, sound KDF
The operators, or developpers, clearly have cryptographic expertise. Choosing Curve25519 over RSA, implementing proper ECDH, and using HC-128 (not amateur AES-CBC) shows sophistication well beyond typical ransomware.
Operational Features
✅ Builder-specific configs: Each sample unique per victim (RaaS model)
✅ Smart optimizations: Panic mode encrypts 10% in seconds vs hours
✅ Custom obfuscation: XOR+LCG like config encryption (unique seed/multiplier)
✅ Metadata tracking: Footer preserves decryption capability
The “panic” mode is particularly clever: on a 10TB server, encrypting just 10% (uniformly distributed) renders everything unusable while completing in minutes. This beats detection/response timelines.
Why It’s Effective
The hybrid encryption means:
- Reverse engineering is futile: No secret key in the binary to extract
- Per-file security: Breaking one file doesn’t help with others
- Builder control: Only they can decrypt (payment enforcement)
- No generic decryptor possible: Each victim has unique builder public key
This is fundamentally different from ransomware with hardcoded keys or weak crypto - those can be broken.